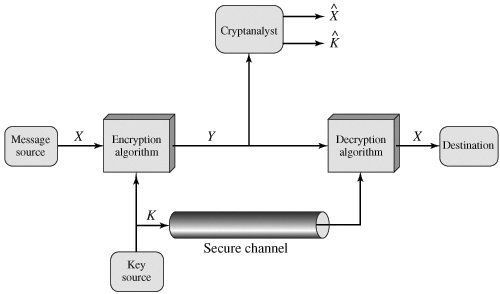
The original Plaintext is converted into apparently random nonsense, called Ciphertext. The Encryption process consists of an algorithm and a key. The key is a value independent of the plain text. The algorithm will produce a different output depending on the specific key being used at the time.Changing the key changes the output of algorithm, the ciphertext.
Once the ciphertext is produced, it may be trasmitted. Upon reception, the ciphertext can be transformed back to the original plaintext by using a descryption algorithm and the same key that was used for encryption.
If we look at picture above, with the message X and the encryption key K as input, the encryption algorithm form the ciphertext.
Y= Ek(X)
The Intended receiver, in possession of the key is able to invert transformation.
X= Dk(Y)
An opponent, observing Y but not having access to K or X, may attempt to recover X or K or both, X and X . It is assumed that the opponent know the encryption (E) and Decryption (D) algorithms. If the opponent is interested in only this particular message, then the focus of the effort is to recover X by generating a plaintext estimate X^. Often, However, the opponent is interest in being able to read future message as well, in which case an attempt is made to recover K by generating and estimate K^.
The Process of attempting to discover X or K or both is known as Cryptanalyst.
-HenSou-



0 komentar:
Post a Comment